Hacking, for the most part in popular culture, has always been misrepresented. The producers of these media focus more on getting the typical “oh look code with alphabets and number, hacking!!” While most of the movies and TV shows are stereotypical and represent hacking in the most cliched way, one show stands out. Yes, I am talking about the hoodie wielding and unforgiving world of the techno-thriller Mr. Robot! Over the years, only NMap has found its way into the movies like Matrix, Die Hard 4 etc. Whereas, the producers of Mr. Robot don’t shy away from embracing hacking for what it is. There have been countless articles about the amount of extensive research they did to make the in-show hacking close to the real thing. They even inspired ProtonMail to introduce a feature known as loggers! Mentioned below are the real tools used in the show which make the show all more unique as it maintains a delicate balance of the story and what is realistically and technically possible:
- Kali Linux
There are a lot of references to Kali Linux. It is a Linux distro made for penetration tester but it is frequently used by hackers as it is jam-packed with hacking tools.
2. Wickr
It is an end-to-end chatting app which has a lot of features like adjustable expiry date for messages. It is used by fsociety in season 2.
3. Tor Browser
The most obvious anonymizing tool is featured in the show. It makes one’s internet activity hard to trace.
4. Raspberry Pi
A small programmable inexpensive computer which is meant for children to learn computer science has found its unusual niche in hobbyists, programmers and hackers due to its cheapness, versatility and simplicity. It was used into the show to remotely hack the heating systems of Steel Mountain.
5. DeepSound
Used extensively throughout the show, used by Elliot to hide people’s identity under regular music. Fun Fact, this technique’s called steganography and the files are on viewable through DeepSound!
6. ProtonMail
The beloved end-to-end encrypted e-mail service which is used by Mr Robot himself! It has been reported that the team behind Mr. Robot researched secured email so much that they even contacted ProtonMail and asked if users can check their login history. The answer, however, was no but the developers liked the idea so much that they introduced account access logs in their V2.0.
7. HDShredder
It is used to securely wipe out all the fsociety’s hard drive before they incarcerate it in the dog pound.
8. John The Ripper
A brute force hacking software which makes thousand of guesses of a Unix password every second and is included in Kali Linux. It is used by Elliot to hack into Tyler Wellick’s system.
9. USB in the parking
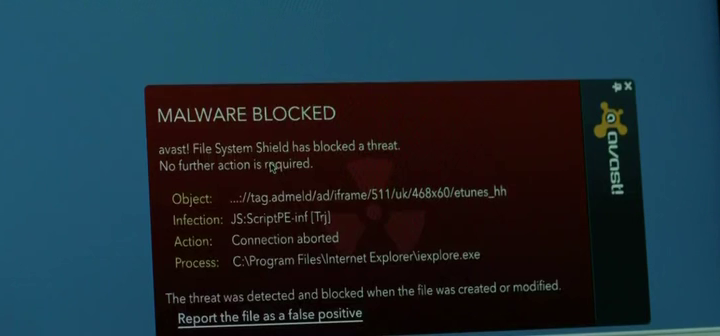
Though not a tool but more of a tactic. The technique of dropping USB sticks in a parking lot where hackers can’t get direct access to infect systems is a well-known trick to get code into a system. In the show however, the malware is caught by Avast anti-virus.
10. btscanner and Bluesniff
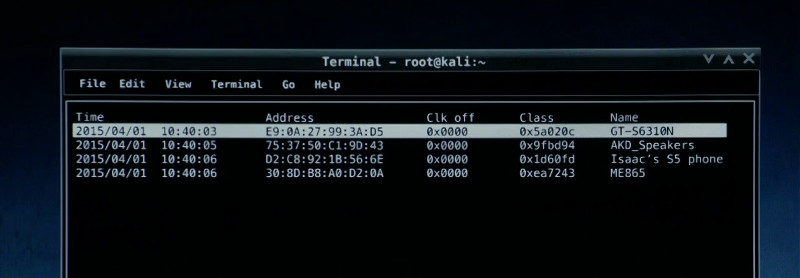
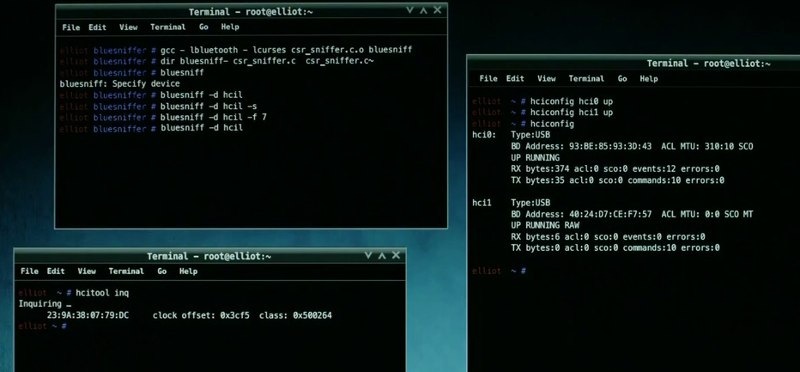
btscanner is used in the show to target phones with Bluetooth access and Bluesniff is used to gain access of a Bluetooth keyboard. btscanner is included in KaliLinux and the operating system in the show is the same OS. Bluesniff is used to drop a Meterpretor shell in the targeted system.
For further reading on bluetooth hacking, consider checking out:
http://allhackernews.com/latest-bluetooth-hacking-techniques-expose-new-attack-vectors-for-hackers/
11. Netscape navigator
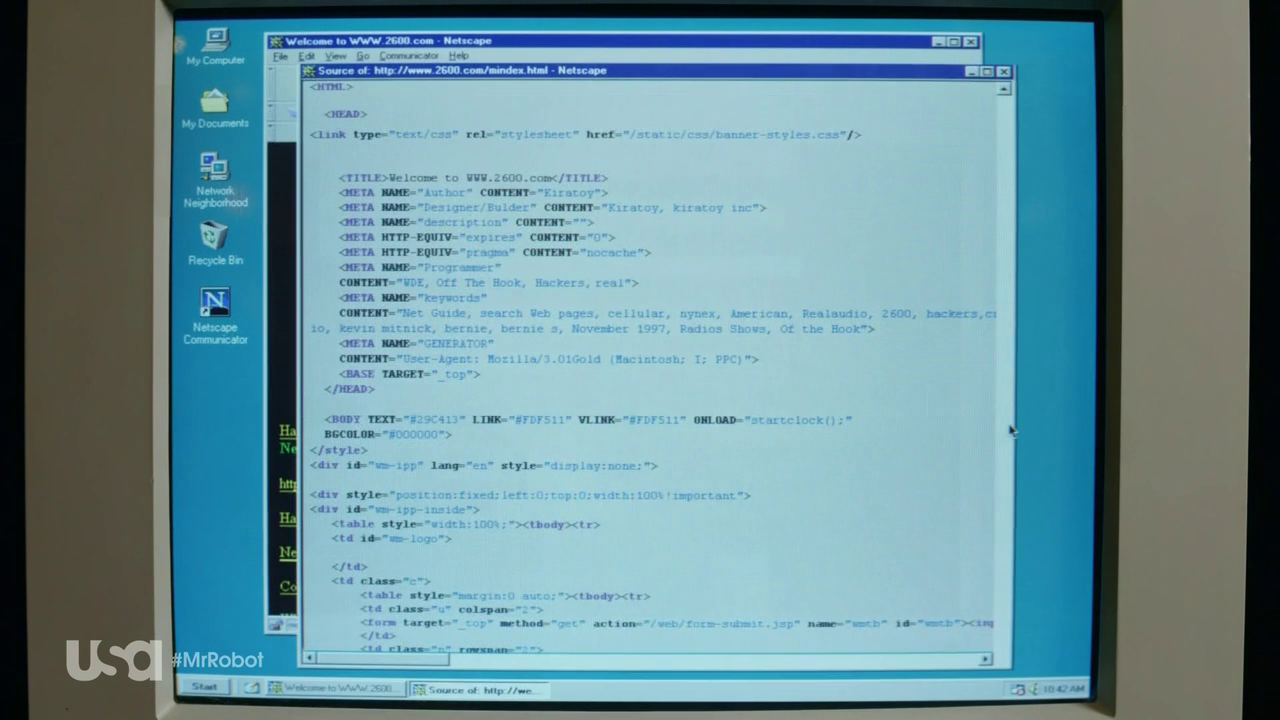
Of all the things they could’ve mentioned and used in the show. When Elliot’s talking to us and telling his baby steps as a hacker. We see a glimpse of his baby steps as a hacker. In the scene, Elliot is viewing the source code of a website (Very advanced right?). Jokes apart, many hackers still prefer Netscape Navigator as it can effective in launching socially engineered attacks on websites like Linkedin.
Well, there you go for all the major tools that were used in the show. This article is just scratching the surface of the extent producers went to ensure the grounded hacking. You can consider looking into the tools used in the show for further reading.